تنشأ المخاطر المتعلقة بتكنولوجيا المعلومات نتيجة للمسؤولية القانونية أو فقدان المهمة بسبب: الكشف غير المصرح به (الخبيث أو العرضي) عن المعلومات أو تعديلها أو إتلافها الأخطاء والإغفالات غير المقصودة انقطاعات تكنولوجيا المعلومات بسبب الكوارث الطبيعية أو من صنع الإنسان
Bshair ahmad
IT infra-structure
الاثنين، 14 أبريل 2025
اهمية التقنية في الحياة
وما هو دور التقنية في حياتنا؟ تلعب التقنية دورًا حيويًا في تحسين وتشكيل وتأثير حياتنا اليومية بطرق عديدة ومتنوعة. من خلال توفير الوسائل السهلة للوصول إلى المعلومات والخدمات، تمكنت التقنية من تخفيف العبء عن الناس وتحسين كفاءتهم. ومن خلال الوصول السريع إلى المعلومات، يمكن للأفراد اليوم الحصول على المعرفة بلمسة زر.
السبت، 29 ديسمبر 2012
my participation about Encryption software
Encryption software
Encryption software is software whose main task is encryption and decryption of data, usually in the form of files on (or sectors of) hard drives and removable media, email messages, or in the form of packets sent over computer networks.
Security
Encryption software executes an algorithm that is designed to encrypt computer data in such a way that it cannot be recovered without access to the key. Software encryption is a fundamental part of all aspects of modern computer communication and file protection and may include features like file shredding.
The purpose of encryption is to prevent third parties from recovering the original information. This is particularly important for sensitive data like credit card numbers.
Encryption choices
Many encryption algorithms exist. The more popular options were submitted to the National Institute of Standards and Technology or NIST for the Advanced Encryption Standard (AES) competition. The winner, Rijndael, got 86 votes while Serpent got 59 votes, Twofish 31 votes, RC6 23 votes and MARS 13 votes. NIST chose Rijndael as its standard. Serpent and Rijndael are in fact somewhat similar; the main difference is that Rijndael is faster (having fewer rounds) but Serpent is more secure[citation needed].
Choosing encryption
There are several factors that affect the choice of an encryption algorithm including speed and security. The simplest method would be an XOR operation, with a constant value 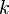 , of each byte of plain text
, of each byte of plain text  , to produce a cipher value
, to produce a cipher value  .
.
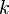 , of each byte of plain text
, of each byte of plain text  , to produce a cipher value
, to produce a cipher value  .
.
Ciphers can be categorized into two general types: public key ciphers and symmetric key ciphers.
Public key systems are based upon algorithms that are at least strongly believed to be "one-way" operations. That is, encryption with one member of a key pair is only easily reversed (decrypted) using the other member of the pair. Further, one member of the pair (the public key) cannot be easily used to determine the other (the private key). Provided the problems posed by the system to cryptanalyst are effectively unsolvable, the system is effectively secure. Such systems are used for key exchanges (for subsequent use of symmetric key ciphers), digital signatures and the like.
Symmetric key ciphers (also referred to as secret key ciphers) are called such because the same key is used for both encryption and decryption. Thus, in order for messages encrypted with a symmetric key cipher to remain secure, the key used must remain secret. Symmetric key ciphers can be further subdivided into stream ciphers and block ciphers.
Stream ciphers typically encrypt plaintext a bit or byte at a time, and are most commonly used to encipher real-time communications, such as audio and video information. The key is used to establish the initial state of a key-stream generator, and the output of that generator is used to encrypt the plaintext.
Block cipher algorithms encrypt blocks of bytes of plaintext a block at a time. The Advanced Encryption Standard algorithm (AES - derived from the Rijndael cipher algorithm) is a block cipher that processes 16 bytes at a time, while its predecessor, the Data Encryption Standard algorithm (DES) encrypted blocks of eight bytes.
A common mistake made by amateur cryptographers is the assumption that because the method is secret, the cipher is secure. This is not usually true. Many "home grown" encryption algorithms reveal the key quite easily when fed a string of identical bytes (e.g., nulls).
The purpose of disseminating an encryption method is to allow the community to evaluate it. If it is indeed secure, then its power lies in the fact that its method has been subjected to scrutiny and found to be sound, not that it is secret
Applications
Encryption can be applied to data in many ways. Common categories are:
- Disk encryption software (also known as OTFE software)
- File/folder encryption
- Database encryption
- Communication encryption software
Network traffic encryption tools
- Generis
- IPSec based
Each of these categories define the range and location of the data to be encrypted, but the process is the same for each
reference
-------------------------------------------------------------------------------------------------------------------------------------------------------------------
in the following link is explain application is safe house is very nice program and free
------------------------------------------------------------------------------------------------------------
the end
الخميس، 27 ديسمبر 2012
my topic
Here
my topic
my
data
infrastructure
?What is Infrastructure Virtualization
Virtual Infrastructure Overview
press here
How Virtualization Works
press here
Virtual Infrastructure Advantages
press here
important-in-virtualization
press here
Types of virtualization
press here
software use in virtualization
press here
Virtualization Issues
press here
security vrtualization
press here
Virtualization for Innovation
press here
?????Is virtualization cloud computing
PRESS HERE
Virtualization and Cloud and Grid
press here
Database virtualization
press here
PDF Book in vrtualization
press here
-------------------------------------------------------------------------------------------------------
finally i would like to enjoy in myblogger
\
and don't forget give me your feedback and comment *_^i Waiting for every one
--------------------------------------------------------------------------------------------------------
press here
How Virtualization Works
press here
Virtual Infrastructure Advantages
press here
important-in-virtualization
press here
Types of virtualization
press here
software use in virtualization
press here
Virtualization Issues
press here
security vrtualization
press here
Virtualization for Innovation
press here
?????Is virtualization cloud computing
PRESS HERE
Virtualization and Cloud and Grid
press here
Database virtualization
press here
PDF Book in vrtualization
press here
-------------------------------------------------------------------------------------------------------
finally i would like to enjoy in myblogger
\
and don't forget give me your feedback and comment *_^i Waiting for every one
--------------------------------------------------------------------------------------------------------
BSHAIR
AHMAD AL-HARBI
الاثنين، 24 ديسمبر 2012
Who Invented Virtualization?
What company "invented" virtualization technology?
A: The long defunct Burroughs Corporation first brought mainframe virtualization to market in the 1960s. But it was not until the then laggard IBM brought it to their 360 line in the 1970s that the concept was legitimized.
I'm willing to make this little bet with you: Most people of a certain age are more than willing to bet folding green that IBM ‘invented' virtualization. Gen-any-letters will bet VMware with confidence. You will win either way.
Today's burgeoning virtualization market is a different story. And in that story,
. VMware is the dad
to read more...
Database virtualization
Database virtualization is the decoupling of the database layer, which lies between the storage and application layers within the application stack. Virtualization at the database layer allows hardware resources to be extended to allow for better sharing resources between applications and users, masking of the physical location and configuration of a database from querying programs, as well as enable more scalable computing.
-------------------------------------------------------------------------------------------------------------------------------------------------------
Database Virtualization Advantages
- Added flexibility and agility for existing computing infrastructure
- Enhanced database performance
- Pooling and sharing computing resources
- Simplification of administration and management
- Increased fault toleance
- reference
---------------------------------------------------------------------------------------------------------
Example of database virtualization :
Oracle Database Support for Server Virtualization
---------------------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------------------------
to learn more:
show this slides
الأحد، 23 ديسمبر 2012
Virtualization and Cloud and Grid
Here will explain
about the relationship between Virtualization and Cloud and
Grid
-------------------------------------------------------------
Cloud
and Virtualization to Support Grid
Infrastructures
Introduce virtualization and cloud from the
perspective of the Grid computing community
• Show the benefits of virtualization and cloud for Grid
computing
• Demonstrate how Grid, virtualization and cloud are
complementary technologies that will cooperate in
future Grid computing infrastructures
• Introduce the RESERVOIR project, European initiative
in virtualization and cloud computing
show this slides to explain more :
---------------------------------------------------------------
An Efficient Use of Virtualization
in Grid/Cloud Environments.
to show more detial
--------------------------------------------------------------------------------
الاشتراك في:
التعليقات (Atom)







